Understanding Malware Types: Protecting Your System from Harmful Software
In the digital age, where technology is deeply integrated into our daily lives, the threat of malware has become a significant concern for individuals and organizations alike. Malware, short for “malicious software,” encompasses a variety of harmful programs designed to damage, disrupt, or gain unauthorized access to computer systems. Understanding the different types of malware is crucial for developing effective strategies to protect your systems. This article will explore common malware types and provide guidance on how to defend against them.
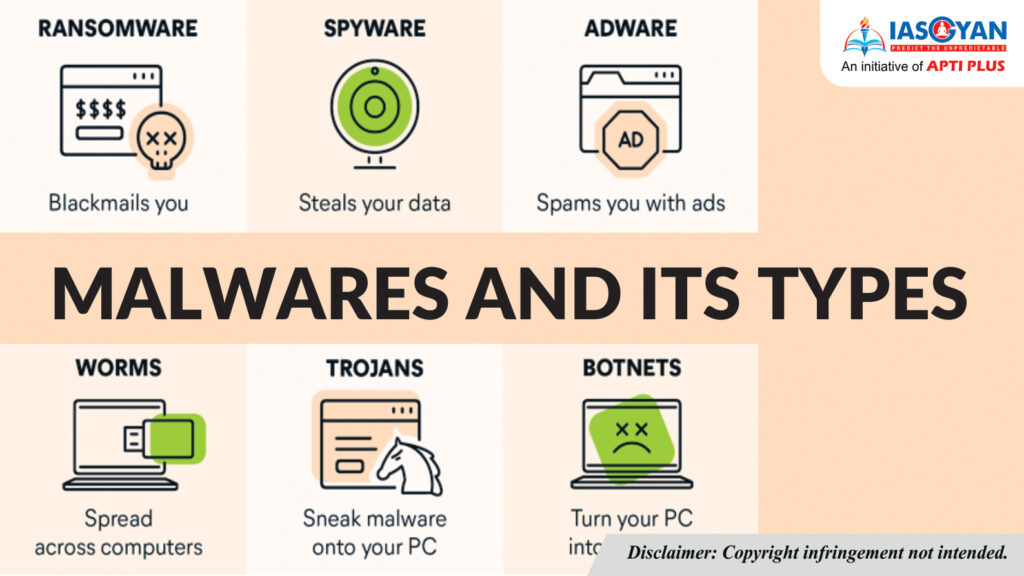
Common Types of Malware
1. Viruses
A virus is a type of malware that attaches itself to legitimate software or files, spreading from one computer to another when the infected file is shared. Viruses can corrupt files, slow down systems, and cause significant data loss. They often require user interaction to spread, such as opening an infected email attachment or downloading compromised software.
2. Worms
Unlike viruses, worms are self-replicating malware that can spread across networks without any user action. They exploit vulnerabilities in operating systems and software to propagate, often leading to network congestion and significant resource consumption. Worms can also create backdoors, allowing attackers to gain unauthorized access to systems.
3. Trojan Horses
Trojan horses masquerade as legitimate software or applications to deceive users into downloading and installing them. Once installed, they can grant attackers access to the victim’s system, allowing them to steal data, install additional malware, or monitor user activity. Unlike viruses and worms, Trojans do not self-replicate; their effectiveness relies on user deception.
4. Ransomware
Ransomware is a particularly insidious type of malware that encrypts a user’s files or locks them out of their system, demanding a ransom payment for decryption. This type of attack can cripple individuals and organizations, often resulting in significant financial losses. Ransomware can spread through phishing emails, malicious downloads, or compromised websites.
5. Spyware
Spyware is designed to secretly monitor user activity and collect personal information without consent. It can track online behavior, log keystrokes, and harvest sensitive data, such as passwords and credit card information. Spyware can be bundled with legitimate software or downloaded through malicious websites.
6. Adware
Adware is software that automatically displays or downloads advertisements, often leading to intrusive pop-ups and browser redirection. While adware may not be malicious in nature, it can degrade system performance and compromise user privacy by tracking browsing habits.
7. Rootkits
Rootkits are stealthy malware designed to gain unauthorized access to a computer system while hiding their presence. They can alter the operating system to conceal other malicious software, making detection and removal extremely challenging. Rootkits can be used to control infected systems and exfiltrate data without detection.
Protecting Your System from Malware
1. Install Comprehensive Security Software
Utilizing reliable antivirus and anti-malware software is one of the most effective ways to protect against malware. Ensure that the software is regularly updated to detect and neutralize the latest threats.
2. Keep Software Updated
Regularly update your operating system and all installed applications to patch vulnerabilities that malware can exploit. Enable automatic updates whenever possible to stay current.
3. Exercise Caution Online
Be vigilant when clicking links or downloading files, especially from unknown or untrusted sources. Phishing emails and malicious websites are common vectors for malware distribution.
4. Use Strong Passwords
Implement strong, unique passwords for all accounts and consider using a password manager to help manage them. This can help mitigate the impact of credential theft from malware.
5. Back Up Data Regularly
Regularly backing up important data ensures that you can recover your files in the event of a ransomware attack or data loss due to malware. Use both local and cloud-based backup solutions for redundancy.
6. Educate Yourself and Others
Awareness and education are vital in defending against malware. Stay informed about common threats and teach others how to recognize and avoid potential risks.
Conclusion
Understanding the various types of malware and their methods of operation is essential for protecting your systems from harmful software. By implementing robust security measures, staying informed about evolving threats, and fostering a culture of awareness, individuals and organizations can significantly reduce the risk of malware infections. In a digital landscape that continues to evolve, vigilance and proactive defense strategies are key to maintaining cybersecurity and safeguarding valuable data.